hack@sayan
CEH Essentials
- 4.721 students
- Last updated 25/7/2023
Descriptions
Organizations rely on cybersecurity experts to protect themselves from threats, but nearly 60% report security talent shortages.1 Prepare for a new career in this high-demand field with professional training from Microsoft — an industry-recognized leader in cybersecurity.
The role of a cybersecurity analyst includes monitoring networks for vulnerabilities or potential threats, mitigating attacks on the network infrastructures, and implementing strategies for data protection. With 95% of fortune 500 companies using Azure, it’s critical for cybersecurity professionals to learn to protect data within an Azure environment.2

Key Points
- Understand the cybersecurity landscape and learn core concepts foundational to security, compliance, and identity solutions.
- Develop and implement threat mitigation strategies by applying effective cybersecurity measures within an Azure environment.
- Understand the vulnerabilities of an organizations network and mitigate attacks on network infrastructures to protect data.
- Demonstrate your new skills with a capstone project and prepare for the industry-recognized Microsoft SC-900 Certification exam.
MODULES
Introduction to Ethical Hacking
Introduction to ethical hacking and penetration testing
Different types of hackers and their motivations
Ethical hacking methodologies and the CEH process
Footprinting and Reconnaissance
Information gathering techniques: passive and active reconnaissance
DNS enumeration, Google hacking, and WHOIS lookups
Social engineering methods for collecting information
Scanning Networks
Network scanning concepts: IP addressing, subnetting, and port scanning
Network discovery and enumeration using tools like Nmap
Vulnerability scanning and analysis using tools like Nessus
Enumeration
Enumeration techniques: NetBIOS, SNMP, SMB, LDAP
User enumeration, email harvesting, and OS fingerprinting
System Hacking
Password cracking methods: brute-force, dictionary attacks, and rainbow tables
Privilege escalation techniques on Windows and Linux systems
Rootkits, malware, and backdoors: detection and removal
Malware Threats
Introduction to different types of malware: viruses, worms, Trojans, ransomware
Malware analysis techniques and tools
Countermeasures and mitigation strategies against malware attacks
Sniffing
Network sniffing concepts and techniques
Sniffing tools like Wireshark and Tcpdump
Detecting and preventing sniffing attacks
Social Engineering
Human-based attacks: phishing, pretexting, tailgating
Influence and manipulation techniques used in social engineering
Defending against social engineering attacks
Denial of Service (DoS)
DoS and DDoS attacks: concepts and impact
Types of DoS attacks: flood attacks, amplification attacks, etc.
Countermeasures and mitigation strategies against DoS attacks
Session Hijacking
Session hijacking techniques: session fixation, session sniffing, and man-in-the-middle attacks
Countermeasures to prevent session hijacking
Hacking Web Servers
Web server architecture and vulnerabilities
Exploiting web server vulnerabilities: SQL injection, cross-site scripting (XSS), command injection
Web application security testing tools and methodologies
Hacking Web Applications
Web application hacking techniques: session management, authentication bypass
Web application vulnerabilities: CSRF, file inclusion vulnerabilities
Web application security best practices and testing methodologies
Hacking Wireless Networks
Wireless network security concepts and vulnerabilities
WEP, WPA, and WPA2 vulnerabilities and cracking
Wireless network security best practices and defenses
Hacking Mobile Platforms
Mobile platform vulnerabilities: Android and iOS
Mobile app security assessment techniques and tools
Best practices for securing mobile devices and applications
IoT and OT Hacking
Introduction to IoT and OT security challenges
Vulnerabilities in IoT and OT devices and networks
Hacking and securing IoT and OT systems
Cloud Computing
Cloud computing security challenges and risks
Cloud service models and deployment models
Securing cloud environments and data
Cryptography
Cryptographic concepts: encryption, hashing, digital signatures
Cryptanalysis techniques and attacks against cryptographic systems
Implementing secure cryptographic solutions
Penetration Testing
Introduction to penetration testing methodologies
Penetration testing planning and execution
Reporting and communication of penetration testing results
Incident Response and Digital Forensics
Incident response process and phases
Digital forensics principles and techniques
Legal and ethical considerations in incident response and forensics
Exam Review and Preparation
Review of key concepts covered in the course
Tips for preparing for the CEH certification exam
Practice exams and mock tests
Keep in mind that this syllabus can be adjusted based on the specific CEH course duration and the participants' background knowledge. Hands-on labs, practical exercises, and real-world scenarios are crucial for providing a comprehensive and effective learning experience. Additionally, ensure that the course covers the latest updates in cybersecurity and ethical hacking practices.
Instructor

Owner
This course includes:
- 62 hours on-demand video
- Full lifetime access
- Access on mobile and TV
- Free Webinar
- Certificate of completion
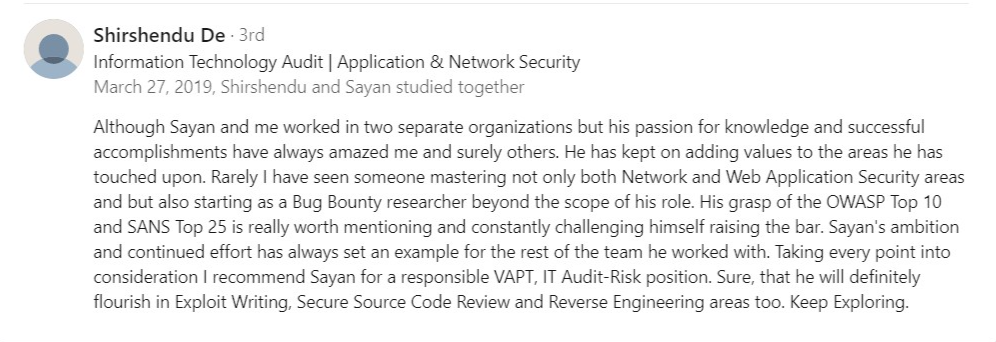
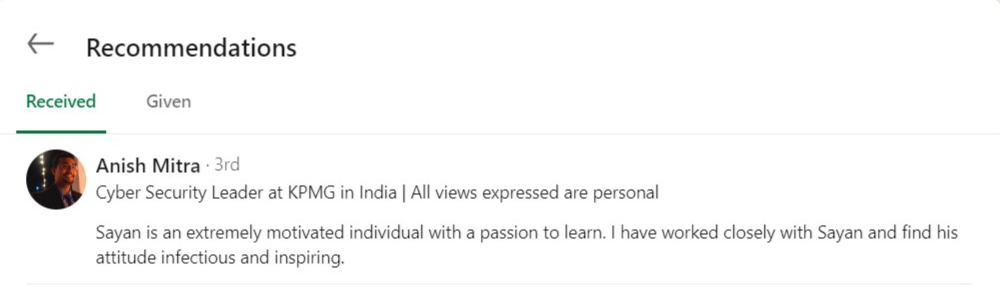
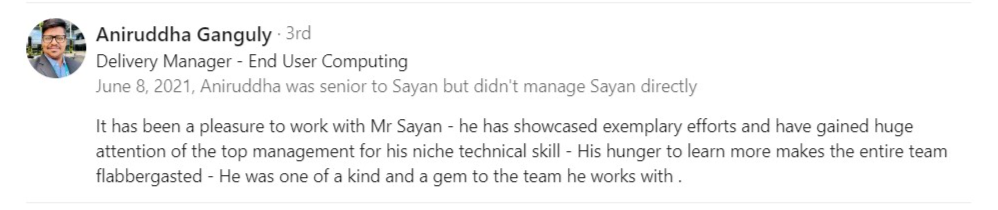
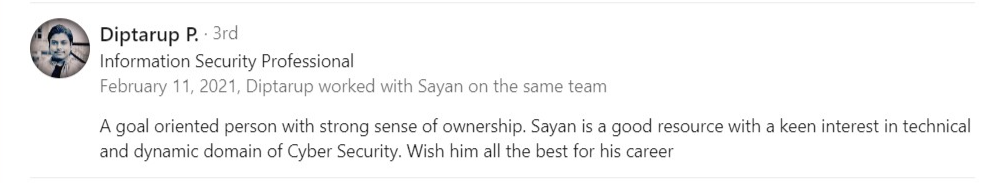
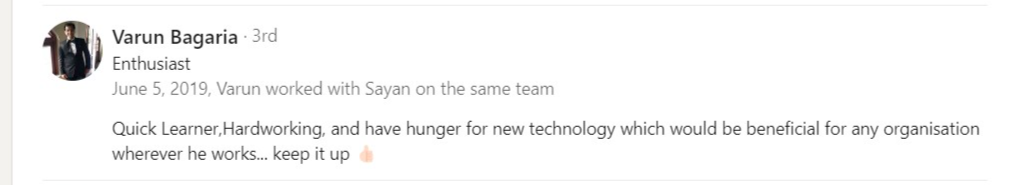
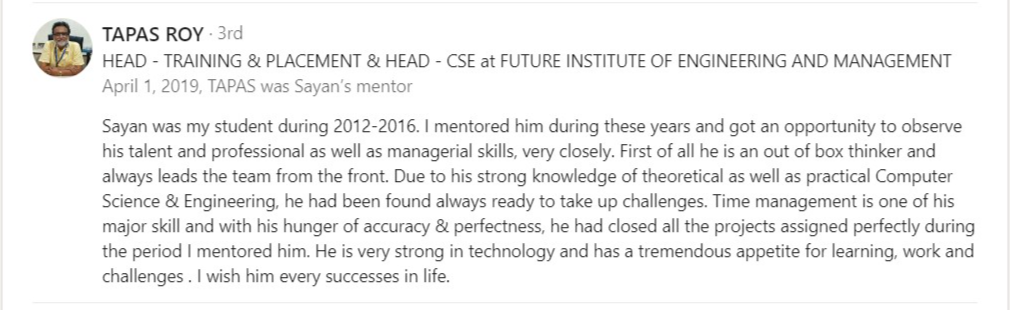

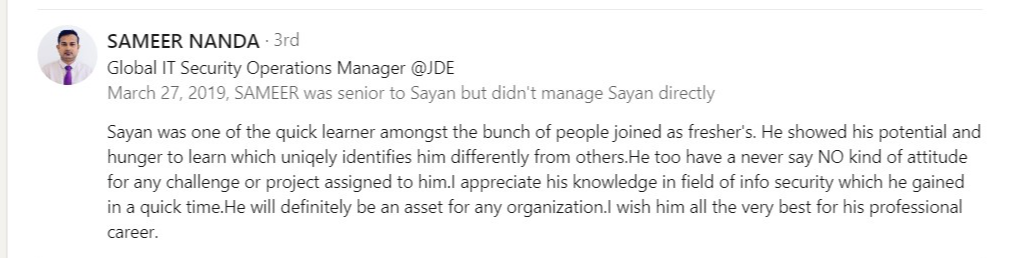

Testimonial
What alumni say about us









